介绍
DenyHosts是用python编写的一个程序。
当你的linux服务器暴露在互联网之中,服务器将会遭到互联网上的扫描软件进行扫描,并试图猜测SSH登录口令。
你会发现,每天会有多条SSH登录失败纪录。那些扫描工具将对你的服务器构成威胁,你必须设置复杂登录口令,并将尝试多次登录失败的IP给阻止掉,让其在一段时间内不能访问该服务器。
它会分析/var/log/secure等日志文件,当发现同一IP在进行多次SSH密码尝试时就会记录IP到/etc/hosts.deny文件,从而达到自动屏蔽该IP的目的
软件的下载地址:
http://jaist.dl.sourceforge.net/project/denyhosts/denyhosts/
https://github.com/denyhosts/denyhosts
DenyHosts安装及配置
CentOS安装
yum -y install denyhosts #我用了这个方式,但无效,原因未知
换个方式安装
wget https://github.com/denyhosts/denyhosts/archive/refs/tags/v3.0.tar.gz
tar xf v3.0.tar.gz
mv denyhosts-3.0/ /application/
cd /application/denyhosts-3.0/
python3.6 setup.py install
默认配置/etc/denyhosts.conf ,如下
[root@li1548-187 denyhosts-3.0]# egrep -v "#|^$" /etc/denyhosts.conf SECURE_LOG = /var/log/auth.log #/这里应该是var/log/secure #ssh日志文件,denyhosts基于此日志内容来判断 HOSTS_DENY = /etc/hosts.deny #控制用户登陆文件 PURGE_DENY = 1w #过多久后清除已经禁止的IP,空表示永远不解禁,我这里设置的是1周 BLOCK_SERVICE = sshd #禁止的服务名,如还要添加其他服务,只需添加逗号跟上相应的服务即可,写个sshd也可 DENY_THRESHOLD_INVALID = 3 #允许无效用户失败的次数 DENY_THRESHOLD_VALID = 3 #允许普通有效用户登陆失败的次数 DENY_THRESHOLD_ROOT = 1 #允许root登陆失败的次数 DENY_THRESHOLD_RESTRICTED = 1 WORK_DIR = /var/lib/denyhosts #denyhosts运行目录,应该是/application/denyhosts-3.0/ ETC_DIR = /etc SUSPICIOUS_LOGIN_REPORT_ALLOWED_HOSTS=YES HOSTNAME_LOOKUP=NO #是否进行域名反解析 LOCK_FILE = /var/run/denyhosts.pid #程序的进程ID IPTABLES = /sbin/iptables ADMIN_EMAIL = root@localhost #管理员邮件地址,可设置告警邮箱 SMTP_HOST = localhost SMTP_PORT = 25 SMTP_FROM = DenyHosts <nobody@localhost> SMTP_SUBJECT = DenyHosts Report ALLOWED_HOSTS_HOSTNAME_LOOKUP=NO AGE_RESET_VALID=5d #用户的登录失败计数会在多久以后重置为0,(h表示小时,d表示天,m表示月,w表示周,y表示年) AGE_RESET_ROOT=25d AGE_RESET_RESTRICTED=25d AGE_RESET_INVALID=10d DAEMON_LOG = /var/log/denyhosts #denyhosts的日志文件 DAEMON_SLEEP = 30s #当以后台方式运行时,每读一次日志文件的时间间隔 DAEMON_PURGE = 1h #当以后台方式运行时,清除机制在 HOSTS_DENY中终止旧条目的时间间隔,这个会影响PURGE_DENY的间隔。 SYNC_UPLOAD = no SYNC_DOWNLOAD = no
修改后的
[root@li1548-187 etc]# cat /etc/denyhosts.conf SECURE_LOG = /var/log/secure HOSTS_DENY = /etc/hosts.deny PURGE_DENY = 1w BLOCK_SERVICE = sshd DENY_THRESHOLD_INVALID = 3 DENY_THRESHOLD_VALID = 3 DENY_THRESHOLD_ROOT = 1 DENY_THRESHOLD_RESTRICTED = 1 WORK_DIR = /application/denyhosts-3.0/ ETC_DIR = /etc SUSPICIOUS_LOGIN_REPORT_ALLOWED_HOSTS=YES HOSTNAME_LOOKUP=NO LOCK_FILE = /var/run/denyhosts.pid IPTABLES = /sbin/iptables ADMIN_EMAIL = root@localhost SMTP_HOST = localhost SMTP_PORT = 25 SMTP_FROM = DenyHosts <nobody@localhost> SMTP_SUBJECT = DenyHosts Report ALLOWED_HOSTS_HOSTNAME_LOOKUP=NO AGE_RESET_VALID=5d AGE_RESET_ROOT=25d AGE_RESET_RESTRICTED=25d AGE_RESET_INVALID=10d DAEMON_LOG = /var/log/denyhosts DAEMON_SLEEP = 30s DAEMON_PURGE = 1h SYNC_UPLOAD = no SYNC_DOWNLOAD = no
手动启动DenyHosts
[root@li1548-187 init.d]# /usr/local/bin/denyhosts.py --config=/etc/denyhosts.conf --daemon
[root@li1548-187 teddylu]# ps -ef|grep denyhosts
root 10623 1 0 02:42 ? 00:00:00 /usr/bin/python3.6 /usr/local/bin/denyhosts.py --config=/etc/denyhosts.conf --daemon
[root@li1548-187 cache]# echo "/usr/local/bin/denyhosts.py --config=/etc/denyhosts.conf --daemon" >>/etc/rc.local
注意:
1.在安装之前要将/var/log/secure日志清空并重启rsyslog => >/var/log/secure => service rsyslog restart,然后再启动denyhosts => /etc/init.d/denyhosts start,不然很可能会有惊喜发生,锁上门才发现钥匙在屋子里
2.用来防止ftp暴力破解好像并不怎么好使,可使用fail2ban。
3. 查看效果
被屏蔽的IP地址,我的服务器每天都会有无数的登陆尝试
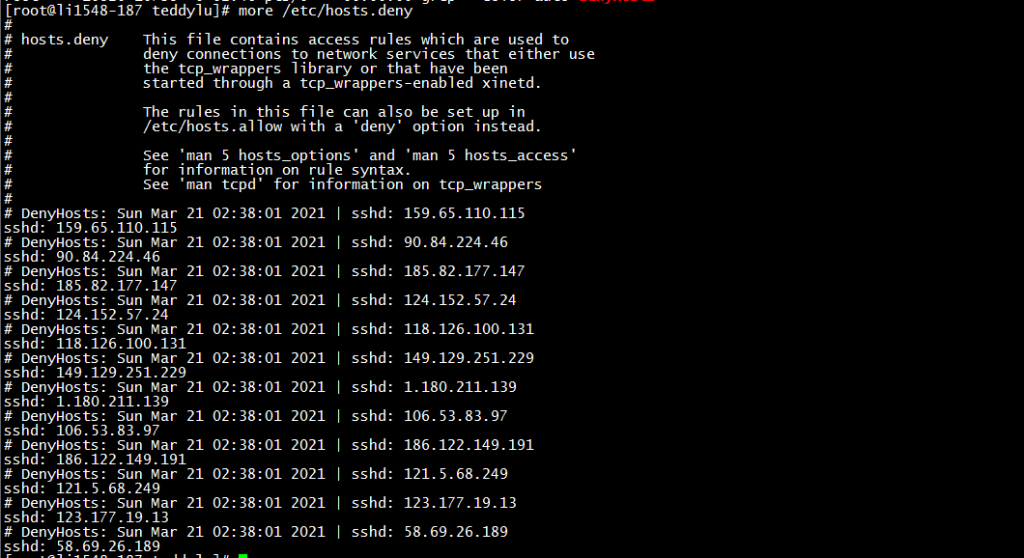
查看/etc/hosts.deny
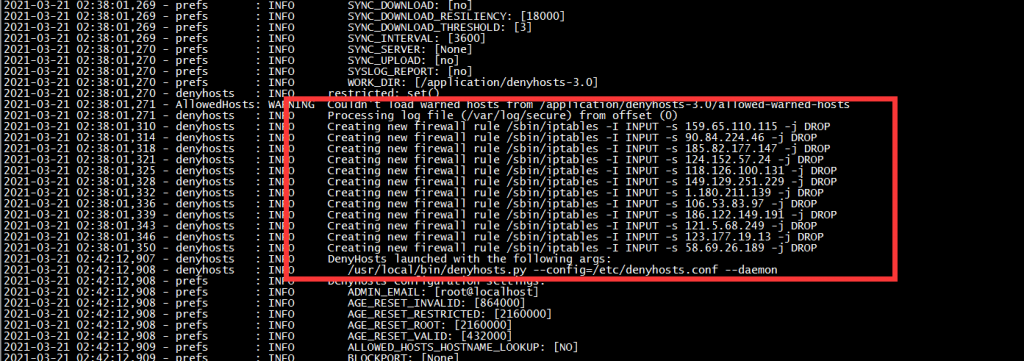
查看/var/log/denyhosts
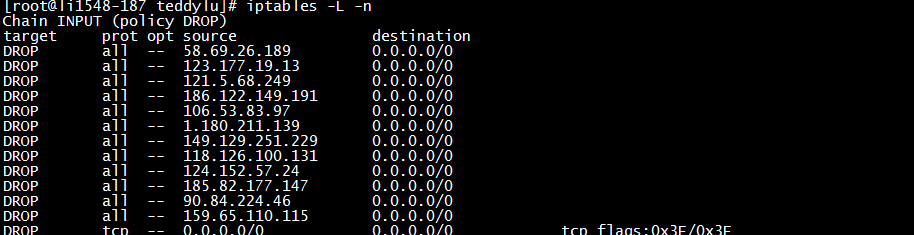
查看iptables
通过上面的log文件,我们可以非常清楚的了解了denyhosts的整个工作原理和流程!!!
参考:
https://chegva.com/2338.html
https://github.com/denyhosts/denyhosts