LDAP是一款轻量级目录访问协议(Lightweight Directory Access Protocol,简称LDAP),属于开源集中账号管理架构的实现,且支持众多系统版本,被广大互联网公司所采用。
一般会将svn,git,VPN,等一系列账号做一个统一管理,ldap是非常好的选择
1.启动ldap和Web UI管理工具,如果想通过浏览器控制 OpenLDAP ,可以使用 phpldapadmin
#启动openladp docker run \ --restart=always \ -v /etc/localtime:/etc/localtime:ro \ -p 389:389 \ -p 636:636 \ --name myopenldap \ --env LDAP_ORGANISATION="ilovesally" \ --env LDAP_DOMAIN="ilovesally.com" \ --env LDAP_ADMIN_PASSWORD="123456" \ -v /openldap/data:/var/lib/ldap \ -v /openldap/conf:/etc/ldap/slapd.d \ --detach osixia/openldap:1.5.0 #启动phpldapadmin(管理工具) docker run \ --restart=always \ -v /etc/localtime:/etc/localtime:ro \ -p 1111:80 \ --name myphpldapadmin \ --env PHPLDAPADMIN_HTTPS=false \ --env PHPLDAPADMIN_LDAP_HOSTS=10.10.20.236 \ --detach osixia/phpldapadmin:0.9.0
由于新建的ldap是没有初始化数据的,所以就需要我们手工创建初始化数据
具体使用方法,可以参考:https://wiki.shileizcc.com/confluence/pages/viewpage.action?pageId=39223519
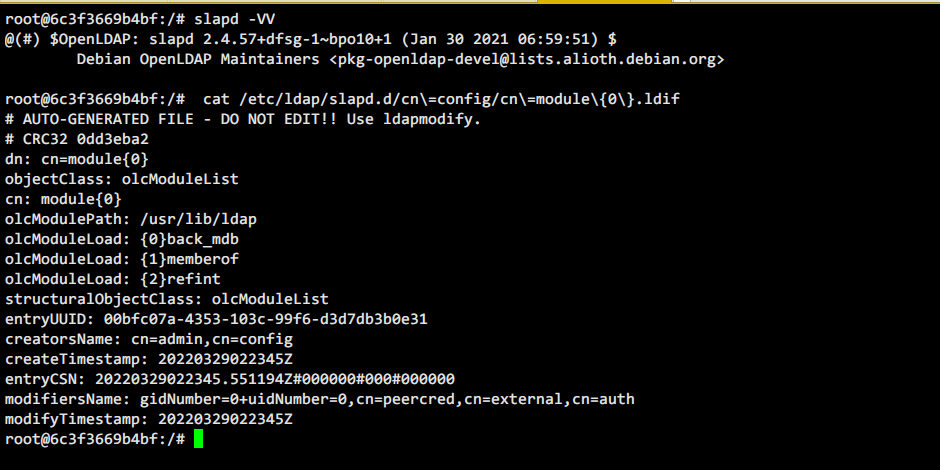
#查看ldap的版本和加载的模块
#查看ldap的配置
slapcat -b cn=config
常用的ldif文件操作
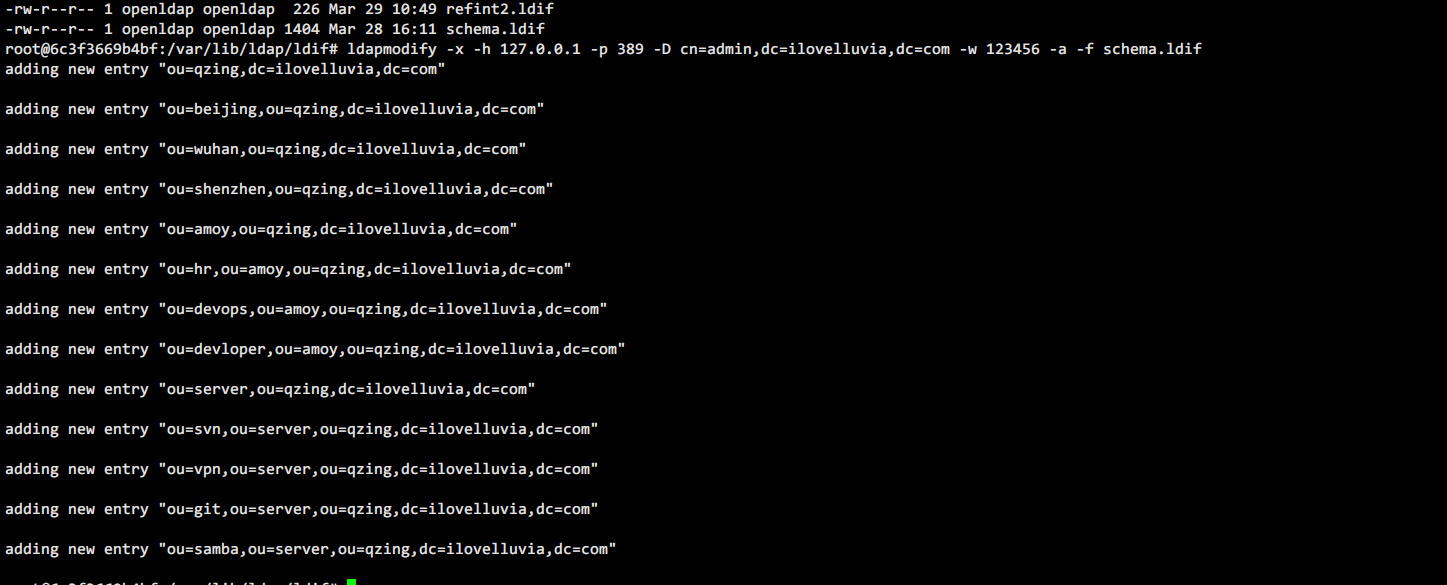
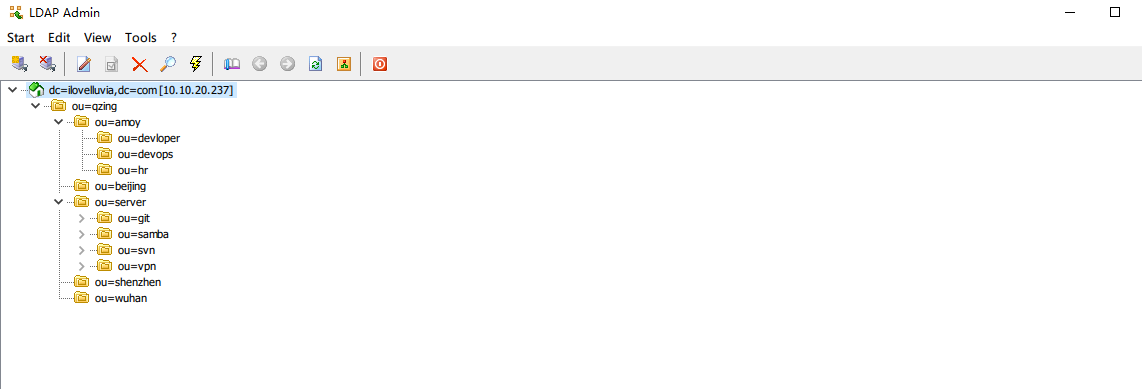
a.企业架构
#企业的组织架构 cat schema.ldif dn: ou=qzing,dc=ilovelluvia,dc=com ou: qzing objectClass: top objectClass: organizationalUnit dn: ou=beijing,ou=qzing,dc=ilovelluvia,dc=com ou: beijing objectClass: top objectClass: organizationalUnit dn: ou=wuhan,ou=qzing,dc=ilovelluvia,dc=com ou: wuhan objectClass: top objectClass: organizationalUnit dn: ou=shenzhen,ou=qzing,dc=ilovelluvia,dc=com ou: shenzhen objectClass: top objectClass: organizationalUnit dn: ou=amoy,ou=qzing,dc=ilovelluvia,dc=com ou: amoy objectClass: top objectClass: organizationalUnit dn: ou=server,ou=qzing,dc=ilovelluvia,dc=com ou: server objectClass: top objectClass: organizationalUnit dn: ou=svn,ou=server,ou=qzing,dc=ilovelluvia,dc=com ou: svn objectClass: top objectClass: organizationalUnit dn: ou=vpn,ou=server,ou=qzing,dc=ilovelluvia,dc=com ou: vpn objectClass: top objectClass: organizationalUnit dn: ou=git,ou=server,ou=qzing,dc=ilovelluvia,dc=com ou: git objectClass: top objectClass: organizationalUnit dn: ou=samba,ou=server,ou=qzing,dc=ilovelluvia,dc=com ou: git objectClass: top objectClass: organizationalUnit
b.创建一个用户,并把其加入到某个组中
#创建用户密码
root@6c3f3669b4bf:/var/lib/ldap/ldif# slappasswd -h {SHA} -s 111111
{SHA}PU8r8H3BvjiyDNbkaUmhBx+dDj0=
#创建导入文件
root@6c3f3669b4bf:/var/lib/ldap/ldif# cat addperson.ldif
dn: uid=luzhihua,ou=devops,ou=amoy,ou=qzing,dc=ilovelluvia,dc=com
uid: luzhihua
cn: luzhihua
sn: luzhihua
givenName: luzhihua
displayName: luzhihua
objectClass: posixAccount
objectClass: top
objectClass: person
objectClass: shadowAccount
objectClass: inetOrgPerson
objectclass: organizationalperson
uidNumber: 1000
gidNumber: 1000
loginShell: /bin/bash
homeDirectory: /home/luzhihua
userPassword: {SHA}PU8r8H3BvjiyDNbkaUmhBx+dDj0=
shadowLastChange: 17654
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
shadowExpire: -1
employeeNumber: A10
homePhone: 0592-xxxxxxxx
mobile: 152xxxxxxxxx
mail: [email protected]
postalAddress: BeiJing
initials: Test
#导入
root@6c3f3669b4bf:/var/lib/ldap/ldif# ldapmodify -x -h 127.0.0.1 -p 389 -D cn=admin,dc=ilovelluvia,dc=com -w 123456 -a -f addperson.ldif
adding new entry "uid=luzhihua,ou=devops,ou=amoy,ou=qzing,dc=ilovelluvia,dc=com"
#创建导入文件
cat >>add_group.ldif<<EOF
dn: cn=projectA,ou=qzing,dc=ilovelluvia,dc=com
objectClass: groupOfUniqueNames
cn: projectA
description: ProjectA all users
uniquemember: uid=luzhihua,ou=devops,ou=amoy,ou=qzing,dc=ilovelluvia,dc=com
EOF
#导入
root@6c3f3669b4bf:/var/lib/ldap/ldif# ldapmodify -x -h 127.0.0.1 -p 389 -D cn=admin,dc=ilovelluvia,dc=com -w 123456 -a -f add_group.ldif
adding new entry "cn=project1,ou=qzing,dc=ilovelluvia,dc=com"
#验证
root@6c3f3669b4bf:/var/lib/ldap/ldif# ldapsearch -LL -Y EXTERNAL -H ldapi:/// "(uid=luzhihua)" -b dc=ilovelluvia,dc=com memberOf
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
version: 1
dn: uid=luzhihua,ou=devops,ou=amoy,ou=qzing,dc=ilovelluvia,dc=com
memberOf: cn=projectA,ou=qzing,dc=ilovelluvia,dc=com
2.制作nginx镜像,加上ldap模块,其中nginx-auth-ldap模块的下载地址是:https://github.com/kvspb/nginx-auth-ldap.git
[root@10-10-20-236 nginx]# cat Dockerfile FROM centos:7.9.2009 MAINTAINER teddylu<[email protected]> # 安装软件 RUN yum -y update && yum -y install epel-release openssl openssl-devel zlib zlib-devel pcre pcre-devel glibc glibc-devel glib2 glib2-devel ncurses ncurses-devel curl curl-devel wget libevent-devel libevent uuid-devel uuid gmake libxml2 libxml2-devel libxslt-devel GeoIP GeoIP-devel GeoIP-data gcc gdb strace gcc-c++ autoconf unzip openldap openldap-devel # 创建用户 #RUN groupadd teddylu #RUN useradd -g teddylu teddylu -s /bin/false # 定义Nginx版本号 ENV VERSION 1.21.1 # 下载并解压文件 RUN mkdir -p /soft && cd /soft && wget http://nginx.org/download/nginx-$VERSION.tar.gz && tar xf nginx-$VERSION.tar.gz # 创建安装目录 ENV NGINX_HOME /application/nginx-1.21.1 RUN mkdir -p $NGINX_HOME #RUN chown -R teddylu:teddylu $NGINX_HOME ADD nginx-auth-ldap-master.zip /soft RUN cd /soft/ && unzip nginx-auth-ldap-master.zip # 进入解压目录 WORKDIR /soft/nginx-$VERSION # 编译安装 RUN ./configure \ --user=root \ --group=root \ --prefix=$NGINX_HOME \ --with-http_ssl_module \ --with-http_v2_module \ --with-threads \ --with-stream \ --with-stream_realip_module \ --with-stream_ssl_module \ --with-stream_ssl_preread_module \ --with-http_realip_module \ --add-module=/soft/nginx-auth-ldap-master \ --with-http_gzip_static_module \ --with-http_stub_status_module RUN make && make install # 设置环境变量 ENV PATH /application/nginx-1.21.1/sbin:$PATH # 暴露端口 EXPOSE 80 EXPOSE 443 # 清理压缩包与解压文件 RUN rm -rf /soft CMD $NGINX_HOME/sbin/nginx -g 'daemon off;' -c $NGINX_HOME/conf/nginx.conf
3.启动nginx(注意需要提前将/application/nginx-1.21.1复制到宿主机中)
docker run \ --name mynginx-ldap \ --restart=always \ -v /etc/localtime:/etc/localtime:ro \ -p 80:80 \ -p 443:443 \ -v /application/nginx-1.21.1/:/application/nginx-1.21.1/ \ -d mynginx-ldap:v1.0
4.nginx配置文件(window2012的AD安装跳过)
#这个是window2012AD的配置
ldap_server openldap {
url ldap://10.10.20.72:389/ou=it,dc=ilovesally,dc=xyz?sAMAccountName?sub?(objectClass=person);
binddn "ilovesally\Administrator";
binddn_passwd xmasp1@admin
connections 10;
satisfy any;
group_attribute memberOf;
group_attribute memberuid;
group_attribute uniquemember;
group_attribute it;
group_attribute_is_dn on;
require valid_user;
}
#这个是openLDAP的配置
url ldap://10.10.20.236:389/dc=ilovesally,dc=com?uid?sub?(objectClass=person);
binddn "cn=admin,dc=ilovesally,dc=com";
binddn_passwd "123456";
#虚拟机配置(这里做了一个反向代理)
[root@10-10-20-236 conf]# cat vhosts/mkdocs.conf
server {
listen 80;
server_name localhost;
location / {
proxy_pass http://10.10.20.236:9999;
auth_ldap "LDAP Authentication!!!!!";
auth_ldap_servers openldap;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Host $server_name;
proxy_read_timeout 1200s;
}
}
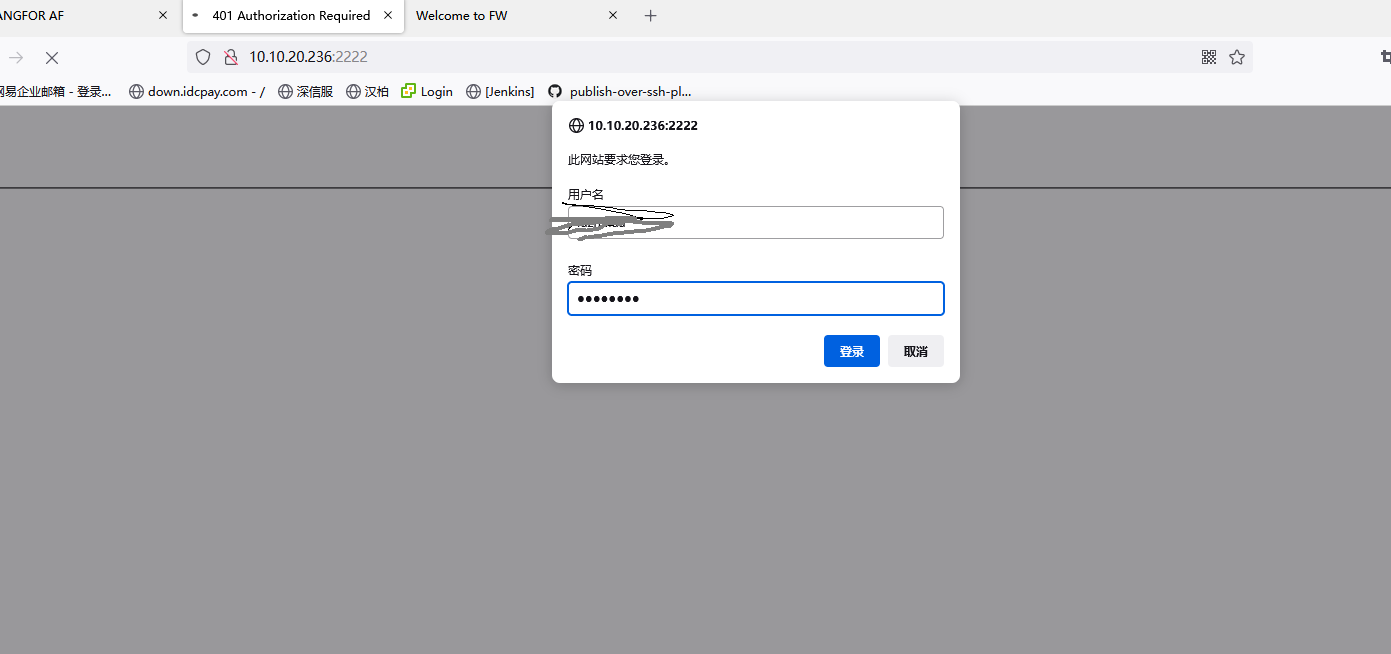
5.看实际效果,一些web服务需要身份验证,这个ldap是非常不错的实现方式
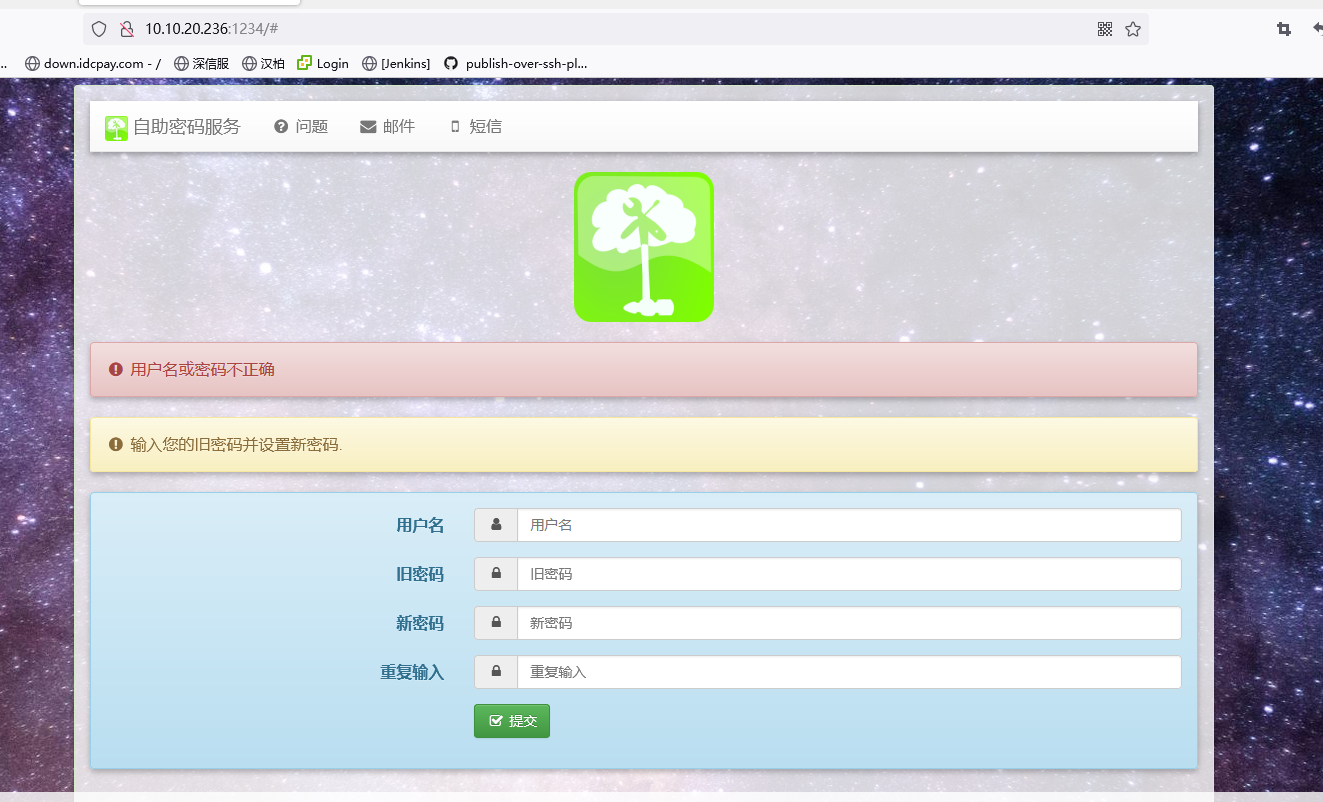
6.自助修改或重置密码服务Self Service Password
Self Service Password是一个PHP应用程序,允许用户在LDAP目录中更改其密码。
该应用程序可以在标准LDAPv3目录(OpenLDAP,OpenDS,ApacheDS,389 DS,RHDS, Sun Oracle DSEE,Novell等)以及Active Directory上。
它具有以下功能:
Samba模式更改Samba密码
活动目录模式
本地密码策略:
最小/最大长度
禁止字符
大写,小写,数字或特殊字符计数器
重用旧密码检查
复杂度(不同类别的字符)
帮助信息
按问题重置
通过邮件重置(通过邮件发送令牌)
通过短信重置(通过外部电子邮件2短信服务)
验证码(Google API)
更改密码后的邮件通知
docker run \ --restart=always \ -v /etc/localtime:/etc/localtime:ro \ -p 1234:80 \ --name myself-service-password \ -v /ssp/conf/:/var/www/conf \ -d ltbproject/self-service-password:1.4.3
配置文件如下:(主要是修改ldap和邮箱的设置)
[root@10-10-20-236 conf]# cat config.inc.php
<?php
$debug = false;
$ldap_url = "ldap://10.10.20.236:389";
$ldap_starttls = false;
$ldap_binddn = "cn=admin,dc=ilovesally,dc=com";
$ldap_bindpw = '123456';
$ldap_base = "ou=People,dc=ilovesally,dc=com";
$ldap_login_attribute = "uid";
$ldap_fullname_attribute = "cn";
$ldap_filter = "(&(objectClass=person)($ldap_login_attribute={login}))";
$ldap_use_exop_passwd = false;
$ldap_use_ppolicy_control = false;
$ad_mode = false;
$ad_options['force_unlock'] = false;
$ad_options['force_pwd_change'] = false;
$ad_options['change_expired_password'] = false;
$samba_mode = false;
$shadow_options['update_shadowLastChange'] = false;
$shadow_options['update_shadowExpire'] = false;
$shadow_options['shadow_expire_days'] = -1;
$hash = "clear";
$hash_options['crypt_salt_prefix'] = "$6$";
$hash_options['crypt_salt_length'] = "6";
$use_ratelimit = false;
$max_attempts_per_user = 2;
$max_attempts_per_ip = 2;
$max_attempts_block_seconds = "60";
$client_ip_header = 'REMOTE_ADDR';
$pwd_min_length = 0;
$pwd_max_length = 0;
$pwd_min_lower = 0;
$pwd_min_upper = 0;
$pwd_min_digit = 0;
$pwd_min_special = 0;
$pwd_special_chars = "^a-zA-Z0-9";
$pwd_no_reuse = true;
$pwd_diff_login = true;
$pwd_diff_last_min_chars = 0;
$pwd_forbidden_words = array();
$pwd_forbidden_ldap_fields = array();
$pwd_complexity = 0;
$use_pwnedpasswords = false;
$pwd_show_policy = "never";
$pwd_show_policy_pos = "above";
$pwd_no_special_at_ends = false;
$who_change_password = "user";
$show_extended_error = false;
$use_change = true;
$change_sshkey = false;
$change_sshkey_attribute = "sshPublicKey";
$who_change_sshkey = "user";
$notify_on_sshkey_change = false;
$use_questions = true;
$multiple_answers = false;
$multiple_answers_one_str = false;
$answer_objectClass = "extensibleObject";
$answer_attribute = "info";
$crypt_answers = true;
$questions_use_default = true;
$questions_count = 1;
$question_populate_enable = false;
$use_tokens = true;
$crypt_tokens = true;
$token_lifetime = "3600";
$mail_attribute = "mail";
$mail_address_use_ldap = false;
$mail_from = "[email protected]";
$mail_from_name = "Self Service Password";
$mail_signature = "";
$notify_on_change = false;
$mail_sendmailpath = '/usr/sbin/sendmail';
$mail_protocol = 'smtp';
$mail_smtp_debug = 0;
$mail_debug_format = 'error_log';
$mail_smtp_host = 'smtps://smtp.qq.com';
$mail_smtp_auth = false;
$mail_smtp_user = '[email protected]';
$mail_smtp_pass = 'vrwlmydtgagacfjj';
$mail_smtp_port = 465;
$mail_smtp_timeout = 30;
$mail_smtp_keepalive = false;
$mail_smtp_secure = 'tls';
$mail_smtp_autotls = true;
$mail_smtp_options = array();
$mail_contenttype = 'text/plain';
$mail_wordwrap = 0;
$mail_charset = 'utf-8';
$mail_priority = 3;
$use_sms = true;
$sms_method = "mail";
$sms_api_lib = "lib/smsapi.inc.php";
$sms_attribute = "mobile";
$sms_partially_hide_number = true;
$smsmailto = "{sms_attribute}@service.provider.com";
$smsmail_subject = "Provider code";
$sms_message = "{smsresetmessage} {smstoken}";
$sms_sanitize_number = false;
$sms_truncate_number = false;
$sms_truncate_number_length = 10;
$sms_token_length = 6;
$max_attempts = 3;
$keyphrase = "ilovesally";
$show_help = true;
$lang = "en";
$allowed_lang = array();
$show_menu = true;
$logo = "images/ltb-logo.png";
$background_image = "images/unsplash-space.jpeg";
$custom_css = "";
$display_footer = true;
$login_forbidden_chars = "*()&|";
$use_captcha = false;
$default_action = "change";
$use_restapi = false;
if (file_exists (__DIR__ . '/config.inc.local.php')) {
require __DIR__ . '/config.inc.local.php';
}
if (!defined("SMARTY")) {
define("SMARTY", "/usr/share/php/smarty3/Smarty.class.php");
}
$presetLogin = "";
if (isset($header_name_preset_login)) {
$presetLoginKey = "HTTP_".strtoupper(str_replace('-','_',$header_name_preset_login));
if (array_key_exists($presetLoginKey, $_SERVER)) {
$presetLogin = preg_replace("/[^a-zA-Z0-9-_@\.]+/", "", filter_var($_SERVER[$presetLoginKey], FILTER_SANITIZE_STRING, FILTER_FLAG_STRIP_HIGH));
}
}
if (isset($header_name_extra_config)) {
$extraConfigKey = "HTTP_".strtoupper(str_replace('-','_',$header_name_extra_config));
if (array_key_exists($extraConfigKey, $_SERVER)) {
$extraConfig = preg_replace("/[^a-zA-Z0-9-_]+/", "", filter_var($_SERVER[$extraConfigKey], FILTER_SANITIZE_STRING, FILTER_FLAG_STRIP_HIGH));
if (strlen($extraConfig) > 0 && file_exists (__DIR__ . "/config.inc.".$extraConfig.".php")) {
require __DIR__ . "/config.inc.".$extraConfig.".php";
}
}
}
7.svn使用ldap登录(AD域控)
#安装软件 yum install -y subversion cyrus-sasl cyrus-sasl-lib cyrus-sasl-plain #修改sasl的用户验证方式为ldap cp /etc/sysconfig/saslauthd /etc/sysconfig/saslauthd.save sed -i 's/MECH=pam/MECH=ldap/' /etc/sysconfig/saslauthd #修改sasl配置文件/etc/saslauthd.conf cat >>/etc/saslauthd.conf<<EOF ldap_servers: ldap://10.10.20.72 ldap_default_domain: ilovesally.xyz ldap_search_base: DC=ilovesally,dc=xyz ldap_bind_dn: ilovesally\Administrator ldap_password: xmasp1@admin ldap_deref: never ldap_restart: yes ldap_scope: sub ldap_use_sasl: no ldap_start_tls: no ldap_version: 3 ldap_auth_method: bind ldap_mech: DIGEST-MD5 ldap_filter:sAMAccountName=%u ldap_password_attr:userPassword ldap_timeout: 10 ldap_cache_ttl: 30 ldap_cache_mem: 32786 EOF #重启sasl服务以应用配置文件并测试是否通过 systemctl restart saslauthd.service testsaslauthd -u user -p 'password' [root@10-10-20-237 ~]# testsaslauthd -u luzhihua -p 'zxc123?!' 0: OK "Success." #修改SVN的sasl配置文件/etc/sasl/svn.conf cat >>/etc/sasl2/svn.conf<<EOF pwcheck_method:saslauthd #用户验证方法 mech_list: plain login #用户验证信息怎么传输 EOF #修SVN的配置并重启 vim /yourrepository/conf/svnserve.conf [general] anon-access = none auth-access = write #password-db = passwd #关闭passwd authz-db = authz #如果要对版本库进行权限控制,开启authz [sasl] use-sasl = true #开启sasl用户验证
参考:
1.https://www.digitalocean.com/community/tutorials/how-to-use-ldif-files-to-make-changes-to-an-openldap-system
2.https://www.liuwg.com/archives/docker-openldap
3.https://github.com/osixia/docker-openldap
4.https://github.com/osixia/docker-phpLDAPadmin5.
5.https://www.liuwg.com/archives/self-service-password
6.https://blog.51cto.com/yht1990/2633627
7.https://amos-x.com/index.php/amos/archives/centos7-nginx-ldap/
8.https://github.com/kvspb/nginx-auth-ldap
9.https://www.ilanni.com/?p=14214
10.https://amos-x.com/index.php/amos/archives/centos7-nginx-add-module/
11.https://www.cnblogs.com/wilburxu/p/9174353.html
12.https://github.com/kvspb/nginx-auth-ldap/blob/master/example.conf
13.https://stackoverflow.com/questions/51149921/how-to-authenticate-nginx-with-ldap
14.https://www.flftuu.com/2019/09/24/nginx-ldap/
15.https://docs.nginx.com/nginx-controller/platform/access-management/manage-active-directory-auth-provider/
16.http://www.liuwq.com/views/%E8%87%AA%E5%8A%A8%E5%8C%96%E5%B7%A5%E5%85%B7/svn-ldap.html#%E5%AE%89%E8%A3%85%E4%B8%8E%E9%85%8D%E7%BD%AE/