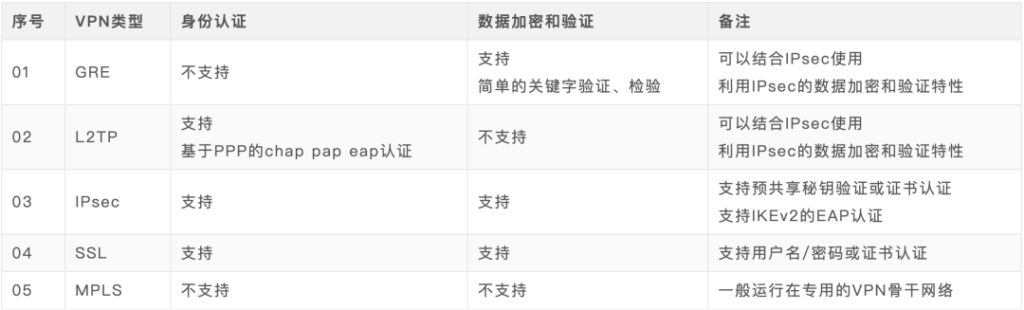
不同VPN隧道身份认证、数据加密、数据验证区别如下表所示:
01 PPTP VPN
点对点隧道协议(PPTP)是由包括微软和3com等公司组成的PPTP论坛开发的一种点对点隧道协议;
基于拨号使用的PPP协议,使用PAP或CHAP之类的加密算法,或者使用Microsoft的点对点加密算法MPPE。
使用PPTP VPN的最大优势在于,无需在windows客户端单独安装客户端软件,默认就支持PPTP VPN拨号连接功能。
适用场景:适合远程的企业用户拨号到企业内部进行办公等的应用。
开源软件:pptp vpn
02 IPsec VPN
IPSec隧道模式是封装、路由与解封装的整个过程。隧道将原始数据包隐藏(或封装)在新的数据包内部;
隧道与数据保密性结合使用时,在网络上窃听通讯的人将无法获取原始数据包数据(以及原始的源和目标);
适用场景:企业异地两地总分公司或多个IDC机房之间的VPN不间断按需连接
开源软件:openswan
03 SSL VPN
SSL VPN提供了数据私密性、端点验证、信息完整性等特性;
SSL独立于应用,因此任何一个应用程序都可以享受它的安全性而不必理会执行细节。http+ssl == https
适用场景:企业异地或者移动用户拨号连接总部实现VPN不间断按需连接
开源软件:openvpn
属于C/S架构的软件,需要单独安装openvpn客户端与服务端。
openvpn 工作原理–部署过程 每一步在做什么
- 需要先关注保证数据安全传输的三要素:数据机密性 数据完整性 身份认证
- 需要掌握秘钥加密技术应用实现;
- 需要掌握证书概念的企业应用;
1.环境说明
系统平台:Centos7.9.2009
OpenVPN 版本:2.4.11
easy-rsa 版本:3.0.8
2.安装软件
yum -y install epel-release && yum -y install openvpn easy-rsa yum -y install openssl openssl-devel lzo-devel
3, EASY-RSA 3.0制作证书
[root@xm-openvpn-10-10-20-231 ~]# mkdir -p /etc/openvpn/easy-rsa [root@xm-openvpn-10-10-20-231 ~]# cp -r /usr/share/easy-rsa/3/* /etc/openvpn/easy-rsa/ [root@xm-openvpn-10-10-20-231 ~]# cp -p /usr/share/doc/easy-rsa-3.0.8/vars.example /etc/openvpn/easy-rsa/vars [root@xm-openvpn-10-10-20-231 ~]# tree /etc/openvpn/ /etc/openvpn/ ├── client ├── easy-rsa │ ├── easyrsa │ ├── openssl-easyrsa.cnf │ ├── vars │ └── x509-types │ ├── ca │ ├── client │ ├── code-signing │ ├── COMMON │ ├── email │ ├── kdc │ ├── server │ └── serverClient └── server
使用 easy-rsa 生成需要的证书及相关文件,将创建CA密钥,VPN server端,client端密钥,DH的key, TLS认证钥匙ta.key
(特别注意)准备签发证书相关变量的配置文件
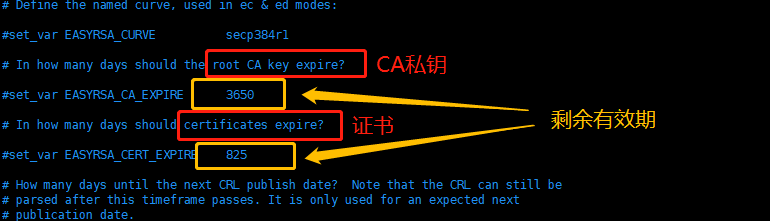
这里CA和OpenVPN服务器颁发的证书的有效期,可适当加长:
vim /etc/openvpn/easy-rsa/vars
CA的证书有效期默为为10年,可以适当延长,比如:36500天
原指令:set_var EASYRSA_CA_EXPIRE 3650
新指令:set_var EASYRSA_CA_EXPIRE 36500
服务器证书默为为825天,可适当加长,比如:3650天
原指令:set_var EASYRSA_CERT_EXPIRE 825
新指令:set_var EASYRSA_CERT_EXPIRE 3650
默认情况下证书的有效期是825天,即两年2个月,如果要长期使用,最好把时间调整长一些
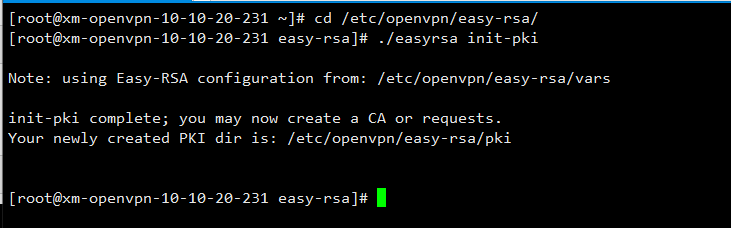
初始化并建立CA证书
[root@xm-openvpn-10-10-20-231 ~]# cd /etc/openvpn/easy-rsa/
[root@xm-openvpn-10-10-20-231 easy-rsa]# ./easyrsa init-pki
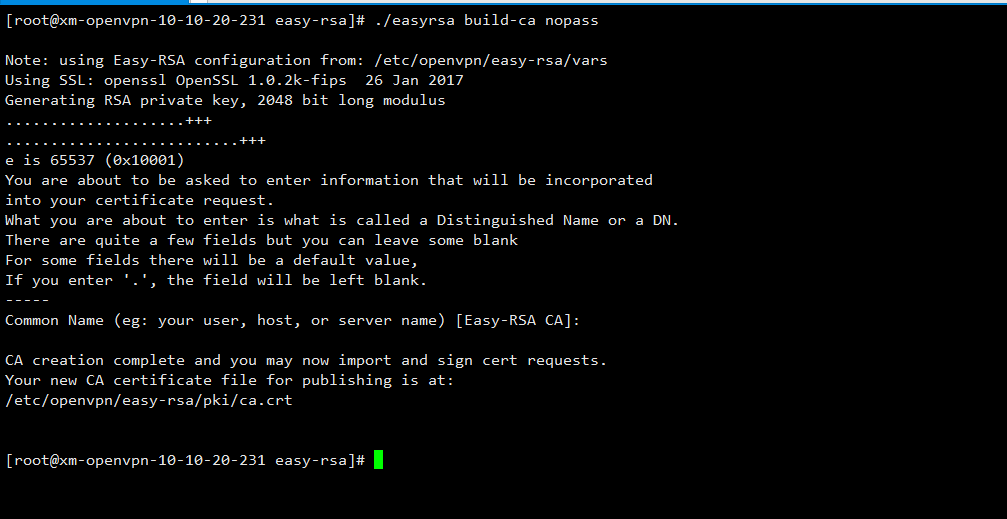
[root@xm-openvpn-10-10-20-231 easy-rsa]# ./easyrsa build-ca nopass
创建vpn服务器证书和私钥,添加nopass 选项,是指不需要为密钥添加密码
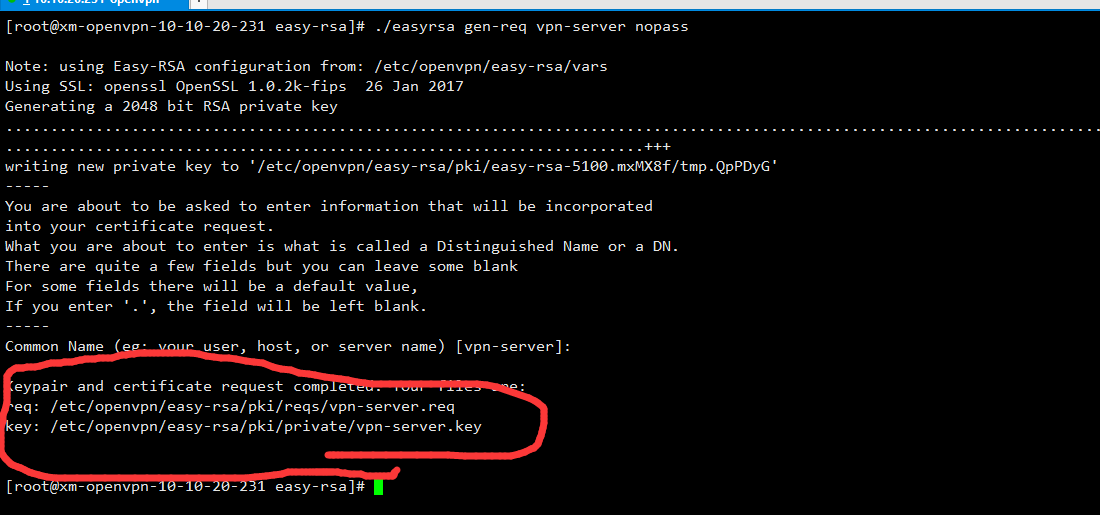
[root@xm-openvpn-10-10-20-231 easy-rsa]# ./easyrsa gen-req vpn-server nopass
用CA证书签名
[root@xm-openvpn-10-10-20-231 easy-rsa]# ./easyrsa sign-req server vpn-server
创建VPN客户端证书和私钥
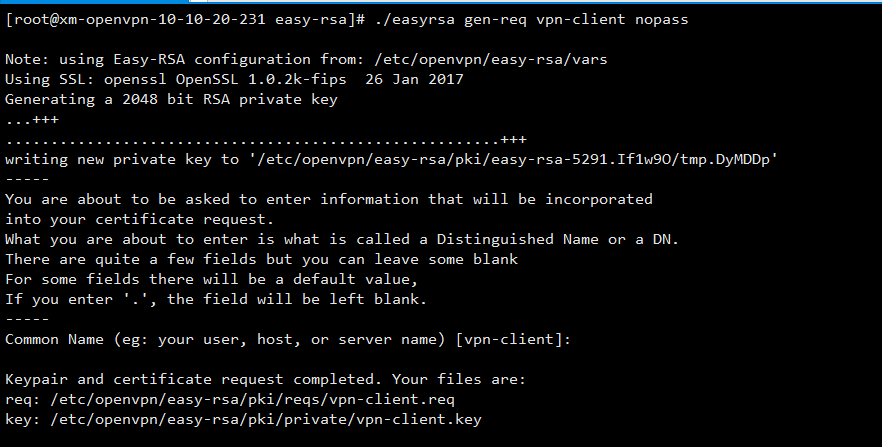
[root@xm-openvpn-10-10-20-231 easy-rsa]# ./easyrsa gen-req vpn-client nopass
用CA证书为客户端证书签名
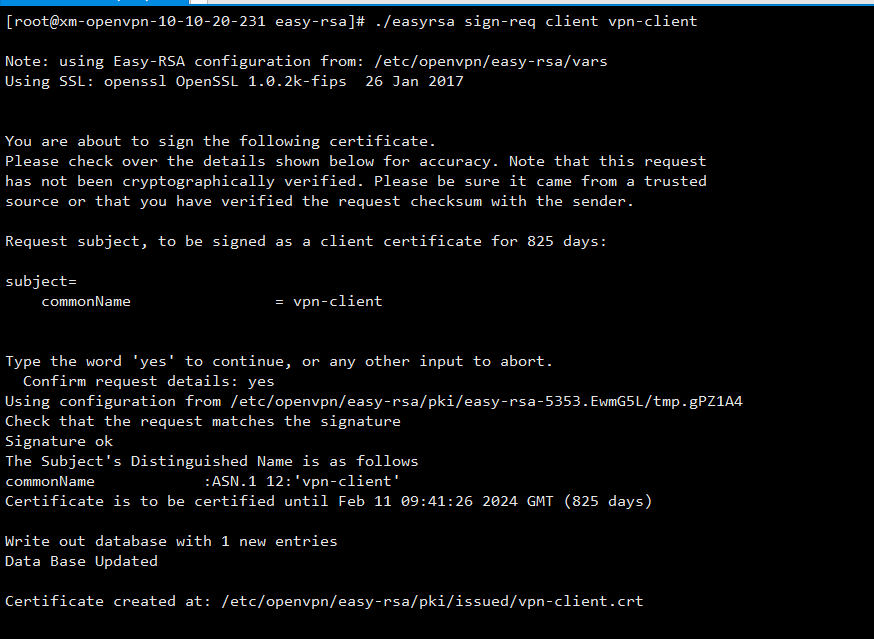
[root@xm-openvpn-10-10-20-231 easy-rsa]# ./easyrsa sign-req client vpn-client
创建DH密钥
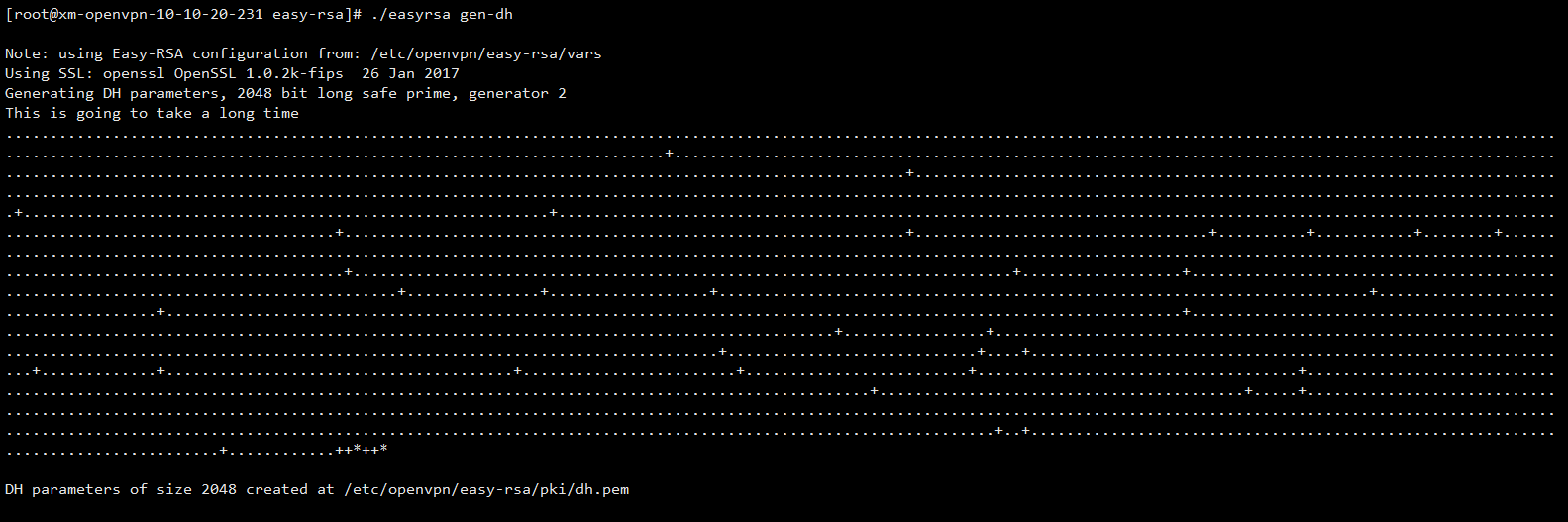
[root@xm-openvpn-10-10-20-231 easy-rsa]# ./easyrsa gen-dh
生成 tls-auth key,主要用于防止 DoS 和 TLS 攻击
[root@xm-openvpn-10-10-20-231 easy-rsa]# openvpn --genkey --secret ta.key
移动到统一管理目录
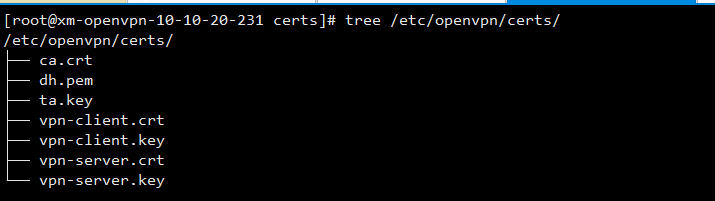
将上面生成的相关证书文件整理到 /etc/openvpn/server/certs (这一步完全是为了维护方便)
[root@xm-openvpn-10-10-20-231 openvpn]# mkdir -p /etc/openvpn/certs [root@xm-openvpn-10-10-20-231 openvpn]# cd /etc/openvpn/certs/ [root@xm-openvpn-10-10-20-231 certs]# cp /etc/openvpn/easy-rsa/pki/dh.pem ./ [root@xm-openvpn-10-10-20-231 certs]# cp /etc/openvpn/easy-rsa/pki/ca.crt ./ [root@xm-openvpn-10-10-20-231 certs]# cp /etc/openvpn/easy-rsa/pki/issued/vpn-server.crt ./ [root@xm-openvpn-10-10-20-231 certs]# cp /etc/openvpn/easy-rsa/pki/private/vpn-server.key ./ [root@xm-openvpn-10-10-20-231 certs]# cp /etc/openvpn/easy-rsa/pki/private/vpn-client.key ./ [root@xm-openvpn-10-10-20-231 certs]# cp /etc/openvpn/easy-rsa/pki/issued/vpn-client.crt ./ [root@xm-openvpn-10-10-20-231 certs]# cp /etc/openvpn/easy-rsa/ta.key ./
创建openVPN日志目录
mkdir -p /var/log/openvpn/
chown openvpn:openvpn /var/log/openvpn
私有网段:(最好使用下面的地址做vpn客户端的ip)
| 10.0.0.0 | 10.255.255.255 | (10/8 prefix) |
| 172.16.0.0 | 172.31.255.255 | (172.16/12 prefix) |
| 192.168.0.0 | 192.168.255.255 | (192.168/16 prefix) |
4,配置 OpenVPN
[root@xm-openvpn-10-10-20-231 openvpn]# cd /etc/openvpn/server [root@xm-openvpn-10-10-20-231 ]# cp /usr/share/doc/openvpn-2.4.11/sample/sample-config-files/server.conf . [root@xm-openvpn-10-10-20-231 ]# cp /usr/share/doc/openvpn-2.4.11/sample/sample-config-files/client.conf .
服务端的配置文件详解:
# 监听的端口号 port 1194 # 服务端用的协议,udp 能快点,所以我选择 udp proto udp # 定义openvpn运行时使用哪一种模式,openvpn有两种运行模式一种是tap模式,一种是tun模式。 # tap模式也就是桥接模式,通过软件在系统中模拟出一个tap设备,该设备是一个二层设备,同时支持链路层协议。 # tun模式也就是路由模式,通过软件在系统中模拟出一个tun路由,tun是ip层的点对点协议。 dev tun # 定义openvpn在使用tun路由模式时,分配给client端分配的IP地址段 server 10.106.0.0 255.255.255.0 # 这条命令可以重定向客户端的网关,在进行翻墙时会使用到 push "redirect-gateway def1 bypass-dhcp" # 向客户端推送的路由信息,如下内容表示客户端连接之后与当前互通 push "route 10.0.0.0 255.255.0.0" # 向客户端推送的DNS信息 push "dhcp-option DNS 223.5.5.5" push "dhcp-option DNS 223.6.6.6" push "dhcp-option DNS 114.114.114.114" # 定义活动连接保时期限 keepalive 10 300 # 加密类型 cipher AES-256-CBC # 启用允许数据压缩,客户端配置文件也需要有这项 comp-lzo # 最多允许连接1000个客户端 max-clients 1000 # 通过keepalive检测超时后,重新启动VPN,不重新读取keys,保留第一次使用的keys persist-key # 通过keepalive检测超时后,重新启动VPN,一直保持tun或者tap设备是linkup的。否则网络连接,会先linkdown然后再linkup persist-tun # 指定日志文件的记录详细级别,可选0-9,等级越高日志内容越详细 verb 4 # 重复日志记录限额 mute 20 # 禁用TSL重协商 reneg-sec 0 # 此选项开启只能使用udp协议。否则会报错error: --explicit-exit-notify can only be used with --proto udp explicit-exit-notify 1 # 客户端1,服务端是0 key-direction 0 # 2.4版本之前使用 tls-auth,如果高于此版本,则用tls-crypt,我用的2.4.8使用了tls-auth,结果连通之后无法访问外网了 tls-crypt /etc/openvpn/server/certs/ta.key 0 # 记录客户端和虚拟ip地址之间的关系。在openvpn重启时,再次连接的客户端将依然被分配和断开之前的IP地址 ifconfig-pool-persist /etc/openvpn/ipp.txt # 使用客户提供的UserName作为Common Name username-as-common-name # 基于mysql进行认证,如不需要可注释掉,注意最后的openvpn_mysql是与后边配置文件名称相呼应的 plugin /etc/openvpn/openvpn-plugin-auth-pam.so openvpn_mysql # CA 根证书路径 ca /etc/openvpn/server/certs/ca.crt # open VPN 服务器证书路径 cert /etc/openvpn/server/certs/server.crt # open VPN 服务器密钥路径 key /etc/openvpn/server/certs/server.key # Diffie-Hellman 算法密钥文件路径 dh /etc/openvpn/server/certs/dh.pem # 指定 log 文件位置 log /var/log/openvpn/server.log log-append /var/log/openvpn/server.log status /var/log/openvpn/status.log
生产环境下完整的VPN服务端的配置文件:
[root@xm-openvpn-10-10-20-231 server]# cat /etc/openvpn/server/server.conf port 11940 proto udp dev tun ca /etc/openvpn/certs/ca.crt cert /etc/openvpn/certs/vpn-server.crt key /etc/openvpn/certs/vpn-server.key dh /etc/openvpn/certs/dh.pem server 100.100.100.0 255.255.255.0 ;push "redirect-gateway def1 bypass-dhcp" ifconfig-pool-persist ipp.txt push "route 10.10.10.0 255.255.255.0 vpn_gateway" push "route 10.10.20.0 255.255.255.0 vpn_gateway" push "route 10.10.21.0 255.255.255.0 vpn_gateway" push "route 192.168.1.0 255.255.255.0 vpn_gateway" push "route 10.231.1.0 255.255.255.0 vpn_gateway" push "route 10.231.2.0 255.255.255.0 vpn_gateway" push "route 10.233.251.0 255.255.255.0 vpn_gateway" push "route 10.233.252.0 255.255.255.0 vpn_gateway" push "route 10.233.254.0 255.255.255.0 vpn_gateway" push "route 192.168.136.0 255.255.255.0 vpn_gateway" push "route 192.168.137.0 255.255.255.0 vpn_gateway" push "route 192.168.138.0 255.255.255.0 vpn_gateway" push "route 192.168.124.0 255.255.255.0 vpn_gateway" push "dhcp-option DNS 114.114.114.114 vpn_gateway" push "dhcp-option DNS 1.1.1.1 vpn_gateway" keepalive 10 300 cipher AES-256-CBC comp-lzo max-clients 1000 persist-key persist-tun verb 3 mute 20 reneg-sec 0 key-direction 0 tls-crypt /etc/openvpn/certs/ta.key 0 username-as-common-name explicit-exit-notify 1 plugin /etc/openvpn/openvpn-plugin-auth-pam.so openvpn_mysql log /var/log/openvpn/server.log log-append /var/log/openvpn/vpnserver.log status /var/log/openvpn/status.logz
注意:
1)通常 openvpn 部署好以后,客户端连接 VPN 后会被配置一些路由,其客户端的路由会被修改为所有的流量都通过 VPN 来传输。
但有时候,我们需要客户端的某些 IP 走 VPN 或者本地网关。这里有两种方法进行 openvpn 的路由配置
第一种方法: 客户端进行配置
在配置文件下增加如下内容:
route-nopull # 客户端连接openvpn后 不从服务端获取路由
max-routes 1000 # 设置路由的最大条数,默认是100,这里可以根据需求修改
route 192.168.0.0 255.255.255.0 net_gateway # 使192.168.0.0/24网段,不走vpn网关
route 192.168.1.0 255.255.255.0 vpn_gateway # 使192.168.1.0/24网段,走vpn网关
注意: 如果配置中有 redirect-gateway def1 则需要先移除
第二种方法: 在服务端进行配置(建议用这种方法)
服务端和客户端的配置略有不同
push “route 192.168.0.0 255.255.255.0 net_gateway” # 将引号中的路由推送到客户端,使192.168.0.0/24网段,不走vpn网关
push “route 192.168.1.0 255.255.255.0 vpn_gateway” # 将引号中的路由推送到客户端,使192.168.1.0/24网段,走vpn网关
注意: 如果配置中有 redirect-gateway 则需要先移除
配置完成后,需要重启 openvpn 服务。
2)如果要使用systemctl来启动,关闭openvpn就必须要将server.conf的配置文件放到/etc/openvpn/server下,否则会报错!!!
#关闭selinux
sed -i '/^SELINUX/s/enforcing/disabled/g' /etc/selinux/config setenforce 0
#开启路由转发和加载BBR模块(优化加速网络)
[root@xm-openvpn-10-10-20-231 conf]# sysctl -p|grep -E "forward|bbr" net.ipv4.ip_forward = 1 net.ipv4.tcp_congestion_control = bbr
#设置防火墙
firewall-cmd --permanent --add-interface=tun0 firewall-cmd --permanent --add-masquerade firewall-cmd --permanent --add-port=11940/udp firewall-cmd --permanent --direct --passthrough ipv4 -t nat -A POSTROUTING -s 100.100.100.0/24 -o ens192 -j MASQUERADE firewall-cmd --reload
#启动 open VPN
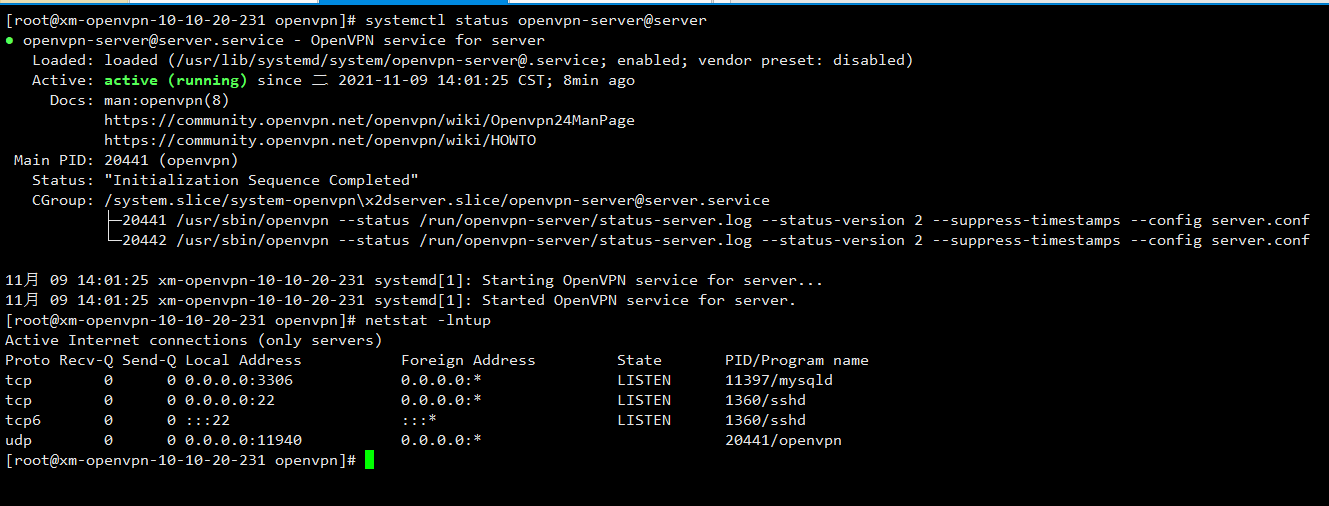
systemctl enable openvpn-server@server systemctl start openvpn-server@server systemctl status openvpn-server@server
PS:这个时候启动是失败的,因为前边配置文件当中引用了 MySQL 认证的配置文件,而这个模块,我们还没有生成
#安装数据库
yum -y install mariadb mariadb-server systemctl enable mariadb systemctl start mariadb
#创建数据库并授权
CREATE DATABASE IF NOT EXISTS openvpn DEFAULT CHARSET utf8; grant all on openvpn.* to openvpn@'localhost' identified by 'openvpn@0592'; flush privileges;
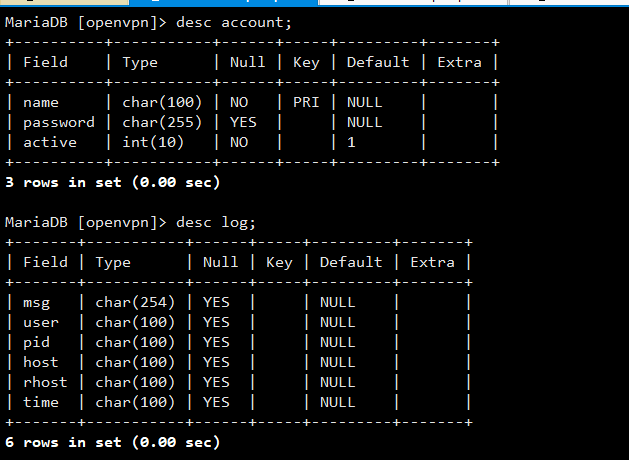
#创建用户表和日志表
use openvpn; create table account(name char(100)not null,password char(255)default null,active int(10)not null default 1,primary key(name)); create table log(msg char (254),user char(100),pid char(100),host char(100),rhost char(100),time char(100));
#创建测试的账号
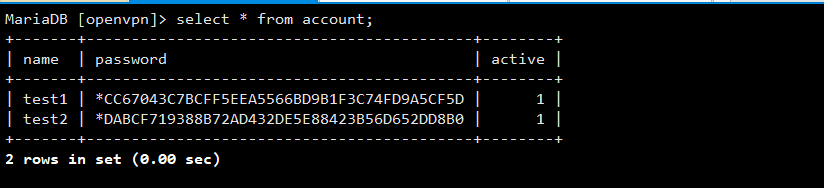
insert into account (name,password) values ('test1',password('123456789'));
insert into account (name,password) values ('test2',password('987654321'));
#查看账号信息
select * from account; +-------+-------------------------------------------+--------+ | name | password | active | +-------+-------------------------------------------+--------+ | test1 | *CC67043C7BCFF5EEA5566BD9B1F3C74FD9A5CF5D | 1 | | test2 | *DABCF719388B72AD432DE5E88423B56D652DD8B0 | 1 | +-------+-------------------------------------------+--------+ 2 rows in set (0.00 sec)
PS:第一列为登录vpn的用户名,第二列为登录的密码,第三列是是否被禁用,1为启用,为0表示不能登录
#修改用户名的密码
update account set password=password('zxc123?!') where name = 'test3';
#优化表结构
mysql> create table users(id int(10)AUTO_INCREMENT,name char(100)not null unique,realname char(100),password char(255)default null,active int(10)not null default 1,comment char(100),primary key(id,name)); Query OK, 0 rows affected, 2 warnings (0.36 sec) mysql> desc users; +----------+-----------+------+-----+---------+----------------+ | Field | Type | Null | Key | Default | Extra | +----------+-----------+------+-----+---------+----------------+ | id | int | NO | PRI | NULL | auto_increment | | name | char(100) | NO | PRI | NULL | | | realname | char(100) | YES | | NULL | | | password | char(255) | YES | | NULL | | | active | int | NO | | 1 | | | comment | char(100) | YES | | NULL | | +----------+-----------+------+-----+---------+----------------+ 6 rows in set (0.00 sec)
#安装认证软件
saslauthd 是一个利用 sasl 资料库进行明文身份验证的守护进程,等会儿配置完毕之后将通过这个工具进行命令行的简单验证。
这步操作之后,也会生成依赖库文件 /usr/lib64/security/pam_mysql.so,后边会提到这个模块
rpm -Uvh http://www.nosuchhost.net/~cheese/fedora/packages/epel-7/x86_64/cheese-release-7-1.noarch.rpm yum -y install pam_mysql pam_krb5 pam pam-devel gcc gcc-c++ cyrus-sasl autoconf epel-release systemctl enable saslauthd systemctl restart saslauthd
配置认证文件
现在想要配置这个工具saslauthd与MySQL的连接,则需要通过如下配置进行定义,配置默认路径在 /etc/pam.d
cat > /etc/pam.d/openvpn_mysql << EOF auth sufficient /usr/lib64/security/pam_mysql.so user=openvpn passwd=openvpn@0592 host=localhost db=openvpn table=account usercolumn=name passwdcolumn=password [where=account.active=1] sqllog=0 crypt=2 sqllog=true logtable=log logmsgcolumn=msg logusercolumn=user logpidcolumn=pid loghostcolumn=host logrhostcolumn=rhost logtimecolumn=time account required /usr/lib64/security/pam_mysql.so user=openvpn passwd=openvpn@0592 host=localhost db=openvpn table=account usercolumn=name passwdcolumn=password [where=account.active=1] sqllog=0 crypt=2 sqllog=true logtable=log logmsgcolumn=msg logusercolumn=user logpidcolumn=pid loghostcolumn=host logrhostcolumn=rhost logtimecolumn=time EOF
注意:
1)此处引用的pam_mysql.so,默认路径为 /usr/lib64/security/pam_mysql.so,此处也可以用绝对路径引用
2)user=openvpn passwd=openvpn@0592 host=localhost db=openvpn table=account,这里的信息是对应上面创建数据库,表,用户,密码
3)这里的openvpn_mysql服务名需要跟openvpn的server.conf中定义的保持一致!!!
# 2个方法验证:
方法一:
如上配置如果都没有问题,那么就可以通过 saslauthd 来进行一下验证了
saslauthd 的用法是 testsaslauthd -u 用户 -p 密码 -s 服务名:
[root@xm-openvpn-10-10-20-231 ~]# testsaslauthd -u test1 -p 123456789 -s openvpn_mysql
0: OK “Success.”
方法二:
[root@xm-openvpn-10-10-20-231 pam.d]# pamtester openvpn_mysql test1 authenticate
Password:
pamtester: successfully authenticated
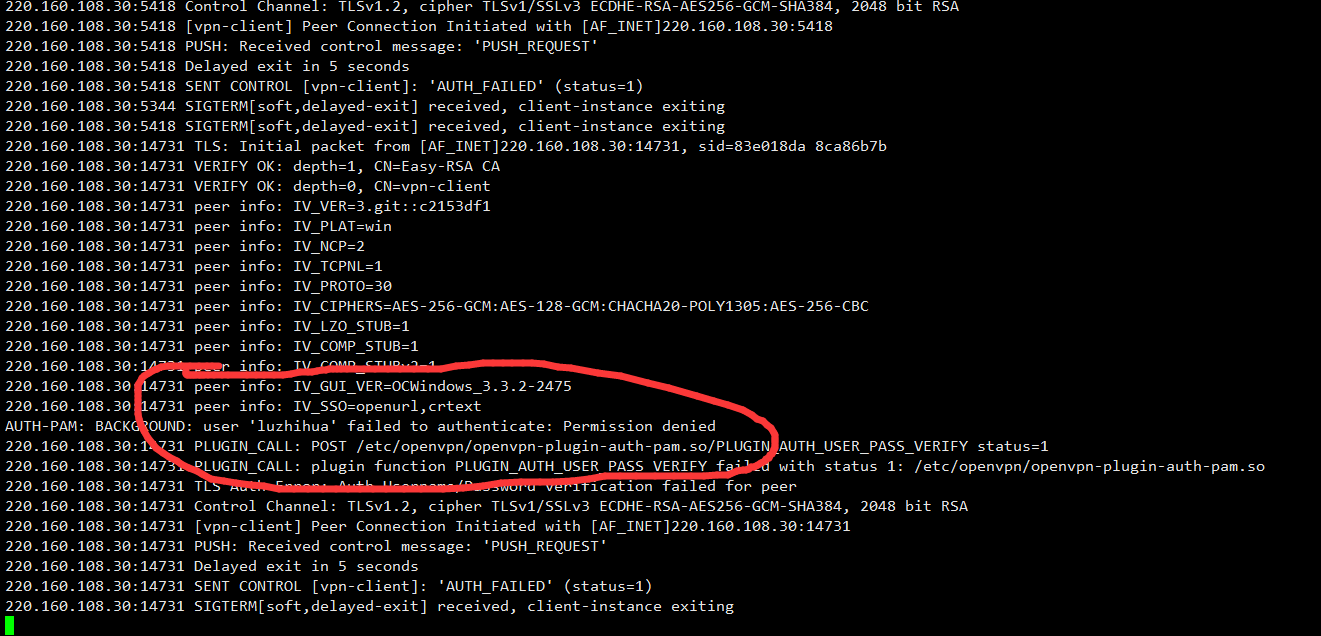
[root@xm-openvpn-10-10-20-231 pam.d]# pamtester openvpn_mysql luzhihua authenticate
Password:
pamtester: successfully authenticated
#安装 openVPN 依赖库
基于 MySQL 认证的 openVPN 使用的服务端配置文件,比普通认证的只多了一行配置:
plugin /etc/openvpn/openvpn-plugin-auth-pam.so openvpn_mysql
注意最后的openvpn_mysql是与后边配置文件名称相呼应的
这行配置的意思是,启用插件,通过 /etc/openvpn/openvpn-plugin-auth-pam.so这个模块儿实现,并对接 saslauthd管理的 openvpn_mysql。
现在还缺少/etc/openvpn/openvpn-plugin-auth-pam.so这个模块,此模块需要通过openVPN的源码编译得来
#下载对应版本的源码包
wget http://swupdate.openvpn.org/community/releases/openvpn-2.4.11.tar.gz tar xf openvpn-2.4.11.tar.gz cd openvpn-2.4.11/ ./configure make
#拷贝模块
cp /root/openvpn-2.4.11/src/plugins/auth-pam/.libs/openvpn-plugin-auth-pam.so /etc/openvpn/
#设置开机启动
systemctl enable openvpn-server@server
systemctl start openvpn-server@server
#用户管理
基于MySQL进行用户管理之后就非常简便了,如果需要新增用户,只需要在account表新增一条数据即可,如果此用户离职了,那么只需要删除这条数据即可或者将active字段的值改为0即可停用
5,客户端配置
下面是完整的客服端的配置文件,再使用自己的用户名密码进行认证即可。
(可以将CA密钥,client端密钥, TLS认证钥匙ta.key的内容合并到同一个文件中,减少冗余)
[root@xm-openvpn-10-10-20-231 ~]# cat /etc/openvpn/client/client.ovpn
client
dev tun
proto udp
sndbuf 0
rcvbuf 0
remote 1.1.1.1 12345 #这里是VPN服务器的ip和端口
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
comp-lzo
verb 3
cipher AES-256-CBC
auth-user-pass
auth-nocache
script-security 3
key-direction 1
<ca>
-----BEGIN CERTIFICATE-----
MIIDNTCCAh2gAwIBAgIJAPkAUAbuZkqaMA0GCSqGSIb3DQEBCwUAMBYxFDASBgNV
BAMMC0Vhc3ktUlNBIENBMB4XDTIxMTEwODA5MjYzNFoXDTMxMTEwNjA5MjYzNFow
FjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAw
ggEKAoIBAQCwuHpp3rI9ofkEZlkvtCcDftU1SUXqX7+0yB1XfVPQF6fohHn1cisn
GKD2ouBmTsjaCBAAlqNgAPRoNu29bF6laV3g9h6dPy/dYYioB5MqpRif04AgOIOx
ilSZeWEFZHHmEGLo32USNIFI+1MH71aW/Uka3ys5+FmHulDrnn6IxI2YslYcP9gp
RVgmyrmtmqwiplKhLVWNsJsdmyhP5FjEdPFR5eFb8sWZ65qo3B1oPWy06e94rgM4
O6lggC37Y6m5eCVow2XV4aul5wvNwebb+7o94kIxTaRzcBj3K/N3GecaWKQ0Q3Gi
Ye2UibR2ib2wreE1TUm2ejXla27T4+OBAgMBAAGjgYUwgYIwHQYDVR0OBBYEFBy8
bhhZLy5ntZ4oBd3R/nqsLwaZMEYGA1UdIwQ/MD2AFBy8bhhZLy5ntZ4oBd3R/nqs
LwaZoRqkGDAWMRQwEgYDVQQDDAtFYXN5LVJTQSBDQYIJAPkAUAbuZkqaMAwGA1Ud
EwQFMAMBAf8wCwYDVR0PBAQDAgEGMA0GCSqGSIb3DQEBCwUAA4IBAQCrc+kF/YIl
Dc6A3sLLu8ieWb47kA6uFgzkr9GJ9ztvjg34QZsVsvIlCtjwjdTl9dNqpxH6DuY/
kh1IeqGJlHnS312uFCaMAZ95odrBImdZw8k/kgxMor3XFq1FHOGhsqxy3boFfnbG
E1AwUvYB2kiHscyXwFbXcNzpjgUhudhuRJIQyngDqyGMucJdhz2jdQLdVoXVwNct
gKRcalWkFETXg1+65xgNPiV9OLJioI48kTbspCubTtfUn8tMUFPHWZz1tf12ZrIr
ZsPQROLlR8+VzViJVhKFB7OlsKzW9wSnynggI5UPawhngK85wljZWkeGckkPvnxy
/mQNbQMdFVQe
-----END CERTIFICATE-----
</ca>
<cert>
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
8a:30:c8:c9:66:13:b3:f6:cf:23:bc:21:e0:17:ec:cc
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=Easy-RSA CA
Validity
Not Before: Nov 8 09:41:26 2021 GMT
Not After : Feb 11 09:41:26 2024 GMT
Subject: CN=vpn-client
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:cd:03:ba:7e:dd:be:ca:2a:e5:f2:a2:4f:2a:15:
e3:b6:2e:f1:28:ad:17:9d:4c:4a:fe:eb:a5:0c:9b:
38:98:0c:8b:9f:ec:8d:91:e4:bc:68:ed:af:68:22:
b1:93:d9:36:ee:4e:3b:00:b8:9e:8d:ea:b9:6b:67:
5d:8e:63:83:bc:9f:ee:90:49:b9:0a:a5:17:62:6e:
9e:33:05:c2:bb:ba:0f:27:a1:93:89:81:88:29:d0:
be:68:48:d4:78:97:4b:d8:87:11:46:9d:92:45:a3:
38:94:f0:76:9c:8e:1c:59:90:df:cc:1f:15:ed:15:
a0:47:2b:19:b7:b7:da:aa:09:2c:c2:8d:2f:7a:15:
4e:d6:43:73:3f:69:03:05:cf:1d:32:cf:21:53:c2:
8b:b6:41:f0:00:5a:bb:64:f4:86:35:ef:5f:21:d2:
a2:62:7a:72:bb:18:0a:60:12:f5:19:6a:56:77:45:
e3:6c:d3:1c:ec:6d:46:1b:45:56:12:19:23:a7:5b:
9d:54:b8:7f:df:29:71:54:1f:41:32:b0:c0:6f:50:
03:7f:81:9a:aa:ba:a9:1d:64:3f:f6:20:b8:be:26:
3f:2b:cb:a3:71:75:03:ca:9e:1d:25:52:22:f6:b3:
e7:c0:b6:07:f4:e0:41:83:83:4e:3d:87:ee:79:ce:
f5:51
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
X509v3 Subject Key Identifier:
39:D0:E1:4B:B2:C9:06:D5:51:BD:4B:68:C5:B9:DE:70:26:EE:CB:55
X509v3 Authority Key Identifier:
keyid:1C:BC:6E:18:59:2F:2E:67:B5:9E:28:05:DD:D1:FE:7A:AC:2F:06:99
DirName:/CN=Easy-RSA CA
serial:F9:00:50:06:EE:66:4A:9A
X509v3 Extended Key Usage:
TLS Web Client Authentication
X509v3 Key Usage:
Digital Signature
Signature Algorithm: sha256WithRSAEncryption
8a:5f:a0:6a:db:aa:3e:1b:3a:63:df:74:ff:e4:9c:3d:e1:5a:
b9:11:54:80:0f:2c:30:29:c9:d6:b6:3a:4a:c6:ae:3a:71:cd:
ad:d1:50:a4:3d:2d:77:44:a0:ea:79:e0:b2:f9:c6:31:ab:79:
ab:63:ab:61:44:1f:e5:fc:96:6b:09:f9:75:ee:07:38:f4:e8:
28:0c:70:3a:db:45:12:08:f4:0e:46:9a:fa:39:38:1f:f5:ed:
80:2c:6a:38:e6:7b:9a:72:1b:66:87:f6:f2:fc:91:b8:1f:0f:
a9:fd:ee:92:10:ee:68:41:a2:b5:37:64:0b:29:96:22:d7:f8:
db:87:28:13:50:c7:4c:0a:bf:af:92:01:a1:4a:a6:ba:c3:fa:
fa:0a:6b:bc:48:48:bc:1c:21:af:60:ca:db:9e:c2:61:fe:24:
eb:06:37:ee:a1:1d:b5:7e:4f:b6:8d:ba:24:3d:9a:fb:49:8b:
8a:65:ea:23:3a:cf:94:ee:4c:23:de:2d:3f:89:2d:36:a3:f1:
7e:fc:47:2e:f0:81:e3:3e:bb:d3:1b:ee:9f:e5:e3:a0:4b:1c:
64:2b:b7:f7:7f:6f:8c:03:d9:cb:86:5f:be:89:68:d6:e3:90:
3f:ac:4a:fa:f7:4e:03:91:25:a3:45:8b:2c:b2:5a:83:8d:5e:
19:c2:03:bb
-----BEGIN CERTIFICATE-----
MIIDTjCCAjagAwIBAgIRAIowyMlmE7P2zyO8IeAX7MwwDQYJKoZIhvcNAQELBQAw
FjEUMBIGA1UEAwwLRWFzeS1SU0EgQ0EwHhcNMjExMTA4MDk0MTI2WhcNMjQwMjEx
MDk0MTI2WjAVMRMwEQYDVQQDDAp2cG4tY2xpZW50MIIBIjANBgkqhkiG9w0BAQEF
AAOCAQ8AMIIBCgKCAQEAzQO6ft2+yirl8qJPKhXjti7xKK0XnUxK/uulDJs4mAyL
n+yNkeS8aO2vaCKxk9k27k47ALiejeq5a2ddjmODvJ/ukEm5CqUXYm6eMwXCu7oP
J6GTiYGIKdC+aEjUeJdL2IcRRp2SRaM4lPB2nI4cWZDfzB8V7RWgRysZt7faqgks
wo0vehVO1kNzP2kDBc8dMs8hU8KLtkHwAFq7ZPSGNe9fIdKiYnpyuxgKYBL1GWpW
d0XjbNMc7G1GG0VWEhkjp1udVLh/3ylxVB9BMrDAb1ADf4GaqrqpHWQ/9iC4viY/
K8ujcXUDyp4dJVIi9rPnwLYH9OBBg4NOPYfuec71UQIDAQABo4GXMIGUMAkGA1Ud
EwQCMAAwHQYDVR0OBBYEFDnQ4UuyyQbVUb1LaMW53nAm7stVMEYGA1UdIwQ/MD2A
FBy8bhhZLy5ntZ4oBd3R/nqsLwaZoRqkGDAWMRQwEgYDVQQDDAtFYXN5LVJTQSBD
QYIJAPkAUAbuZkqaMBMGA1UdJQQMMAoGCCsGAQUFBwMCMAsGA1UdDwQEAwIHgDAN
BgkqhkiG9w0BAQsFAAOCAQEAil+gatuqPhs6Y990/+ScPeFauRFUgA8sMCnJ1rY6
SsauOnHNrdFQpD0td0Sg6nngsvnGMat5q2OrYUQf5fyWawn5de4HOPToKAxwOttF
Egj0Dkaa+jk4H/XtgCxqOOZ7mnIbZof28vyRuB8Pqf3ukhDuaEGitTdkCymWItf4
24coE1DHTAq/r5IBoUqmusP6+gprvEhIvBwhr2DK257CYf4k6wY37qEdtX5Pto26
JD2a+0mLimXqIzrPlO5MI94tP4ktNqPxfvxHLvCB4z670xvun+XjoEscZCu3939v
jAPZy4Zfvolo1uOQP6xK+vdOA5Elo0WLLLJag41eGcIDuw==
-----END CERTIFICATE-----
</cert>
<key>
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDNA7p+3b7KKuXy
ok8qFeO2LvEorRedTEr+66UMmziYDIuf7I2R5Lxo7a9oIrGT2TbuTjsAuJ6N6rlr
Z12OY4O8n+6QSbkKpRdibp4zBcK7ug8noZOJgYgp0L5oSNR4l0vYhxFGnZJFoziU
8HacjhxZkN/MHxXtFaBHKxm3t9qqCSzCjS96FU7WQ3M/aQMFzx0yzyFTwou2QfAA
Wrtk9IY1718h0qJienK7GApgEvUZalZ3ReNs0xzsbUYbRVYSGSOnW51UuH/fKXFU
H0EysMBvUAN/gZqquqkdZD/2ILi+Jj8ry6NxdQPKnh0lUiL2s+fAtgf04EGDg049
h+55zvVRAgMBAAECggEAUELKa0pynAEpXtEOPwKs0DEWdn81RH6OybgFOKc4A8a9
jtF0Jw6ueEG9Lv6OGLysFaWI0eJ1KEghaRvhc5IgC+Ns6Q4DpFg3jHCT/JOfxhC0
SCaodOfCH+S59me0zrUkm1NdfxDHJ/4bc6ukM+wqyyG9i9MLqXKS+em0usj+kRws
ztauXdh0ukwu2UteaqSQ+QLN2gDHJS0GHJUnvWzUPit4xD+fq//ISnLIvBuKwxQl
N2yfT/YCUVSrA7WbdKUUuurtc40MpYdC3w24Ch3BQlvieJ0B1x0E4VDF3tLIOTeO
3Jvvg3PmKu8filNE39kkFC0m4snmKqyP79bXIapmQQKBgQDxCHQpMVbIoJfSU4iE
YX8wkWWYjfqzSJq0/CVL0oIu8yYFixPXqAYhwwd51/CIiXzO2T43nrcII932H9y5
l2g2rG82RJrKgpn09TqnkwCfC63X3B5BT6bcVOdUGR+TV+yxM1wyWwtgsUPVc0Df
nCWGOJzhm63U865fy87RSjzGyQKBgQDZvrZsCtV3qhyvdthn1R+qZvbw18Eb43qt
RqXsEa17hSld5uxAYVF7H3I+yO1sYutDCMisjDF4hJns45DFKojC6fHWOH27j93/
PHQo1iil+QyilqG3NKJke2cwGGz3LqaXTEpnKm8WuSdomQuIqxEXNsRbo+7Gb52/
iN+wO70WSQKBgQDdJ4iNkzuxcchbr1F/RYXSJlY1l3ADuAZbMU93NntEYMzuISHf
qceWir/9R+jnHl9p22J+3h3KVj5+adW4Y/e20phoDqKIVTS10ZwzzWmwhKLJgKox
+sd7OlvWigayxuXh4OIjQe46letLmihYA4lake9AAfuJfNzuAK6O0bLaIQKBgGN7
RHD8SicP62cnDxvxPTRnMm86w5lwRr4fxvKh6PbEEfA67rlDPSzZYyLYPdEFKKNJ
whVDP97mBkU6ewv5sN4McFcFHDyzMCPKhO+bWJrrvCAUXfIL9B2gW7aXkkEkaSw6
yMt1kad6FE0vjxtzvK00cmXD8fVrTVESwdAMmwkxAoGBAOcc5Ip2DU9LDHnJChsj
eLnMJfuo5nfJC92CFmQ/9wF5/AsxdK7h1cTxMe5OKzwBwCh6KfzTOpp4TxHkFtD/
HzHUR11MRswLF76gCx6JZg81u2BtWSlNiIQKIh+3L58pegZpPdO6xyHQUR1pt0mW
fHuJqXSC/AIYXLGqszLrS8vj
-----END PRIVATE KEY-----
</key>
<tls-crypt>
#
# 2048 bit OpenVPN static key
#
-----BEGIN OpenVPN Static key V1-----
aaf2ff88b7cb8d3288a18a5cfef5fa5b
cab86cf3861b9e277adc394370ce5ec3
a6a0fc852806e7002f5671d355aec735
280c09ec4c92bc81cb6f7a16a9defe08
5da3ae82fd99825f0d9e388d5fdbcadf
1f2052762187ba92ea29b9a390367909
103e5cb53bdd2373787de1daae24a583
b286356f62dc4ad89b48c289905b26e3
fa7a64802087b0d9e3521acbe2e8e2ae
4e397afb2e8b23d4d3c93847df62f9f6
7d4aa57ad2674f155eca261b127bd6f3
bba86086cf28d57075dbdf4b4101e41c
b36956a50fcee43909f582ab65e496e6
9fd2c256f3f0e682109a96dc92f8718d
74531d9d1a9794839b62d68712c75303
91f03b1c7f366a2889515536babfe122
-----END OpenVPN Static key V1-----
</tls-crypt>
注意:
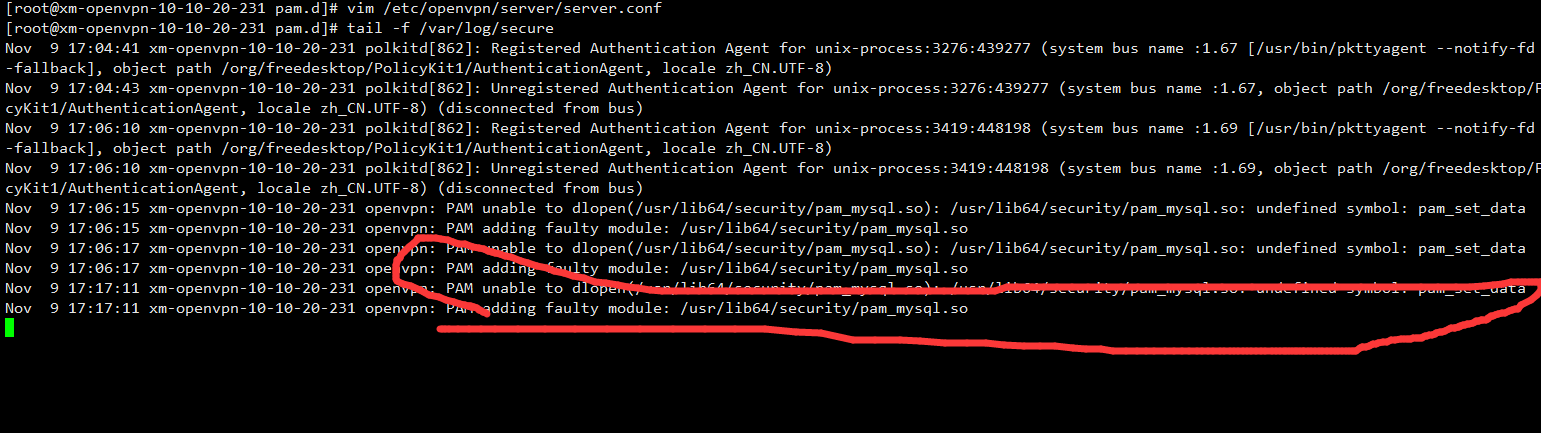
pam_mysql不能直接用yum install pam_mysql安装,系统自带的版本是0.7的,使用这个版本的话会导致后边OpenVPN连接的时候认证不成功,
/var/log/secure日志中会一直报下边错误
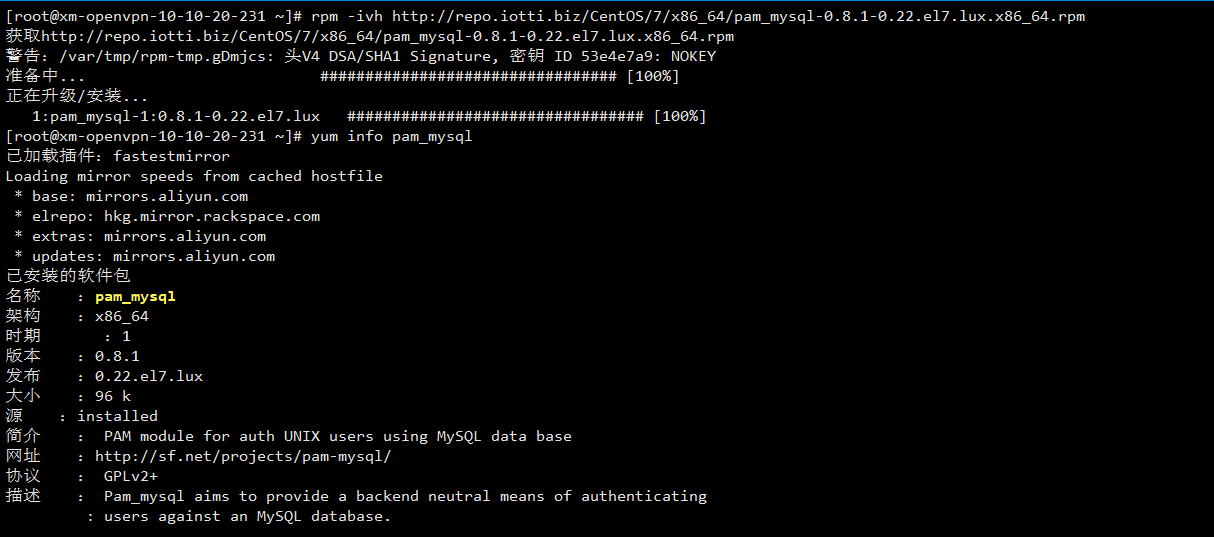
#安装pam_mysql包,版本8.0
[root@xm-openvpn-10-10-20-231 ~]# rpm -ivh http://repo.iotti.biz/CentOS/7/x86_64/pam_mysql-0.8.1-0.22.el7.lux.x86_64.rpm
客户端验证
我们上边已经有了两个测试用户,现在就用其中一个,进行验证。
1.要连接到 open VPN 服务端首先得需要一个客户端软件,但是也可以使用官方的,客户端非常丰富。
在 Mac 下推荐使用 Tunnelblick (opens new window),下载地址:https://tunnelblick.net/。
Tunnelblick 是一个开源、免费的 Mac 版 open VPN 客户端软件。其特点是体积小,相比官方的软件而言。
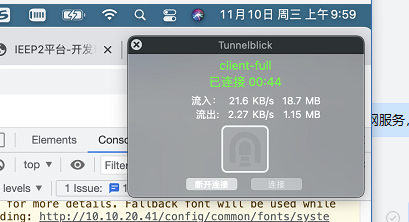
下载之后进行安装,安装方式非常简单,直接将上边生成的配置文件下载到本地,双击 client.ovpn即可自动安装到 Tunnelblick 客户端当中,添加之后的配置可以在界面中查看,如下:
权限细分:
主要是参考官方的文档:https://openvpn.net/community-resources/how-to/
Configuring client-specific rules and access policies
Suppose we are setting up a company VPN, and we would like to establish separate access policies for 3 different classes of users:
- System administrators — full access to all machines on the network
- Employees — access only to Samba/email server
- Contractors — access to a special server only
| Class | Virtual IP Range | Allowed LAN Access | Common Names |
| Employees | 10.8.0.0/24 | Samba/email server at 10.66.4.4 | [variable] |
| System Administrators | 10.8.1.0/24 | Entire 10.66.4.0/24 subnet | sysadmin1 |
| Contractors | 10.8.2.0/24 | Contractor server at 10.66.4.12 | contractor1, contracter2 |
参考:
1)https://forums.openvpn.net/viewtopic.php?t=28261
2)https://www.linuxprobe.com/centos7-config-openvpn-one.html
3)https://www.linuxprobe.com/centos7-config-openvpn-two.html
4)https://wiki.eryajf.net/pages/3809.html
5)https://openvpn.net/community-resources/how-to/
6)https://blog.dianduidian.com/post/openvpn%E4%BD%BF%E7%94%A8mysql%E8%AE%A4%E8%AF%81/
7)https://6xyun.cn/article/97
8)https://mp.weixin.qq.com/s/ibJ6JsTAaM72dLPODsfdNQ
9)https://www.cnblogs.com/panda-xin/p/15740987.html